In the new era, both cybersecurity teams and hackers are using AI to their advantage, so what is AI and how cybersecurity vendors leverage this technology in their solutions.
In this article we had put together the top 10 companies in AI cybersecurity to see different solutions and scenarios about how to use AI in this complicated landscape.
What is AI?
Artificial intelligence, or AI, is a technology that enables computers and machines to simulate human intelligence processes.
AI can work alone or can be combined with other technologies like sensors, geolocation, robotics, etc., to perform tasks that would otherwise require human intelligence or intervention. Digital assistants, GPS guidance, and generative AI tools (like Open AI’s Chat GPT) are just a few examples of AI in the daily news and our daily lives.
What are AI cybersecurity vendors?
AI Cybersecurity vendors are companies specialized in developing and providing cybersecurity solutions powered by artificial intelligence (AI) and machine learning (ML) technologies.
These companies use advanced algorithms and data analytics to detect, prevent, and respond to cyber threats in real-time.
Imagine that you are working as a security engineer in one of the mid-sized companies, and you are receiving 200K alert everyday related to cybersecurity events from your system, for sure you will not be able to deal with all of those alerts as human so you will need the help of AI algorithms which can analyze large amounts of data and detect patterns that are indicative of a cyber threat.
Top 10 Cybersecurity vendors
Here are the top 10 cybersecurity vendors who are involving the AI technology in their solutions:
Fortinet
Fortinet turned its firewall expertise into leadership positions in NGFW, web application firewalls (WAF), unified threat management (UTM) and adjacent markets like software-defined wide area networks (SD-WAN) and enterprise virtual private networks (VPNs).
The Fortinet Security Operations Solution uses AI and advanced analytics to monitor activity across users, devices, networks, emails, applications, files, and logs and detect anomalous or malicious actions that humans may easily overlook.
The solution also allows security teams to orchestrate, automate, and augment Centralized incident investigation and remediation efforts for a faster and more consistent response.
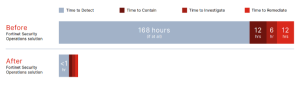
On average, customers using the Fortinet Security Operations Solution reduced their time to detect and contain attacks From 180 hours to under an hour (minutes, in most cases) and then to investigate and remediate in 10 to 15 minutes.
Gartner rating 4.7/5
Trellix
Trellix (formerly FireEye and McAfee Enterprise) is a privately held cybersecurity company that was founded in 2022. It has been involved in the detection and prevention of major cybersecurity attacks. It provides hardware, software, and services to investigate cybersecurity attacks, protect against malicious software, and analyze IT security risks.
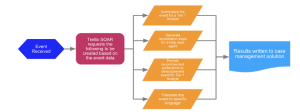
Trellix uses AI-guided investigations to swiftly assess the risk of cyber detection events. This approach reduces the signal-to-noise ratio and shortens response times.
For over six years Trellix solution has been using AI-guided investigations adding a big value with streamlined and efficient SOC investigative workflows.
In addition Trellix used AI in different use cases such as:
- Protecting against data leakage when employees are using GenAI via a Data Security solution that prevents sensitive data from being exposed
- Using AI driven analytics for greater data accuracy and predictive analysis in the realm of Threat Intelligence to help combat threat actors who are also leveraging AI.
- Augmenting existing workflows that require many manual steps and triage processes that GenAI can handle with speed and scale.
- Automating the creation of security content such as SOAR playbooks, YARA or Sigma rules, and searches in threat hunting tools like EDR.
Gartner rating 4.4/5
Skyhigh
Skyhigh Networks was founded in 2011 to protect an organization’s sensitive data by providing visibility, control, and usage of cloud services.
On November 2017, McAfee, an American global computer security software company, announced a definitive agreement to acquire Skyhigh Networks. The deal closed in January 2018.
In March 2021, McAfee announced that its enterprise business was acquired by Symphony Technology Group (STG), and in March 2022, STG relaunched the cloud portfolio, including the former Skyhigh Networks, as Skyhigh Security.
SSE solutions, powered by AI technologies, offer unparalleled visibility and control over data, ensuring that organizations can operate securely in the cloud and beyond.
Integrating AI into SSE solutions can lead to several groundbreaking benefits:
- Enhanced Threat Intelligence: AI algorithms can analyze traffic patterns at the edge, detecting anomalies and potential threats with greater accuracy.
- Predictive Analytics: By leveraging AI, SSE solutions can predict potential security breaches based on historical data and emerging threat patterns.
- Automated Response: AI can automate responses to common threats, reducing the need for manual intervention.
- User Behavior Analysis: AI can monitor user behavior at the edge, identifying any deviations from the norm.
Gartner rating 4.6/5
Checkpoint
Check Point Software Technologies is a global leader in cyber security solutions, dedicated to protecting corporate enterprises and governments worldwide.
Check Point Infinity Platform provides cutting-edge solutions to defend against the most sophisticated cyber-attacks. Check Point portfolio includes Check Point Harmony to secure the workforce, CloudGuard to secure the cloud, and Quantum to secure the network.
ThreatCloud AI – The brain behind Check Point cyber defense, help to deliver the highest catch rate for known and unknown threats, ThreatCloud AI leverages 50+ AI engines and big data gleaned from hundreds of millions of sensors to stop phishing, ransomware, DNS, and malware attacks, as it helps to Block never-before-seen phishing, malware and zero-day attacks for which no IoCs, signatures or patches are available, also IoCs are shared across your entire stack in less than two seconds, including clouds, mobile, IoT, networks, and endpoints.

Infinity Copilot can help to accelerate the daily tasks, Proactively fine-tune controls, and Reduce mean time to respond.
Gartner rating 4.4/5
Elastic
Elastic is a leading platform for search-powered solutions, and it helps everyone — organizations, their employees, and their customers — find what they need faster, while keeping applications running smoothly, and protecting against cyber threats is part of their portfolio.
When you tap into the power of Elastic Enterprise Search, Observability, and Security solutions, you’re in good company with brands like Uber, Slack, Microsoft, and thousands of others who rely on Elastic to accelerate results that matter.
Elastic introduces Elastic AI Assistant, the open, generative AI sidekick powered by ESRE to democratize cybersecurity and enable users of every skill level.
Elastic’s open roots and rapid innovation provides all users access to powerful technology to solve their unique business challenges. The rapid advancements of generative AI have allowed Elastic to take the next step of making these capabilities available to every security analyst, it allows users to interact with Elastic Security for tasks such as alert investigation, incident response, and query generation or conversion using natural language.
Gartner rating 4.4/5
Palo Alto
Palo Alto Networks, is an AI cybersecurity company located in the USA, offers a wide range of products and services. The company’s products include firewall appliances, software, support and maintenance, security management solutions, and more.
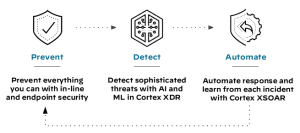
Palo Alto Networks solutions for the SOC use artificial intelligence and machine learning to find important security events without generating low-value alerts that require analyst time, attention, and manual remediation.
Cortex is Palo Alto Network’s AI-based continuous-security platform, which continually evolves to help the SOC stop the most sophisticated threats. Cortex includes Cortex XDR, Cortex XDR Agent, and Cortex XSOAR. Cortex stitches all of the managed endpoints, network, and cloud events together. Because these various stacks witness only part of the buildup of an attack, Cortex uses AI to learn which events in one system drive attention to another system. Using AI and ML, Cortex also identifies unknown and highly evasive threats targeting your network.
Gartner rating 4.4/5
Zscaler
Using zero trust principles, Zscaler helps IT move away from legacy network infrastructure to achieve modern workplace enablement, infrastructure modernization, and security transformation.
Zscaler define the framework for IT transformation with a model that centers around a software-defined policy-controlled architecture that enables secure connection of users to applications or services.
Zscaler had used the AI technologies to deliver many capabilities to their customers to help them stop advanced cyberattacks, simplify zero trust adoption, and ensure great user experiences with:
- Zero trust security for users, powered by AI
- AI-Powered Cloud Browser Isolation
- AI-Powered Phishing Detection
- AI-Powered C2 Detection
- Cyber Risk Assessment
- Contextual Alerts
- Next-gen ZTNA, powered by AI
- AI-Powered App Segmentation
- Private App Protection
- Attacker Deception
- Privileged Remote Access
- Private App Isolation
- Digital experience monitoring, powered by AI
- AI-Powered Root Cause Analysis
- Software Inventory Metrics
- Robust API Integrations
- ISP Insights
Gartner rating 4.5/5
Crowedstrike
CrowdStrike is one of the leading global AI cybersecurity companies with a diverse range of products and services such as endpoint protection detection and response, threat intelligence, next-generation antivirus, incident response, and ransomware protection.
Charlotte AI is the CrowdStrike solution helps to accelerate security operations using GenAI.
Charlotte AI is built on a revolutionary multi-model architecture that’s continuously trained on trillions of daily events and world-class threat intelligence, tuned with expert-driven context and anonymized usage. Models are transparently changed and updated, optimizing the speed and accuracy of all outcomes.
Charlotte helps to Get fast, actionable answers to plain-language questions to understand your environment, investigate attacks, rapidly write technical queries, or get AI-powered recommendations for reducing risk, and Take immediate action with native workflow automation to eradicate threats, including killing processes, quarantining suspicious files, or executing Real Time Response scripts on your behalf.
Gartner rating 4.7/5
Getvisibility
Getvisibility is an AI cybersecurity company empowers organizations to take control of their data and protect it from all potential threats. Their tailored AI technology provides real-time visibility, understanding, security and access to an organization’s sensitive data, so they can focus on what truly matters – their business.
Getvisibility Tailored AI seamlessly connects your tech landscape, ensuring comprehensive visibility across cloud, on-premises, and in-between. Eliminating blind spots, it provides a complete view of your tech assets, integrating effortlessly with leading platforms. Whether starting your data security journey or with an extensive framework, Getvisibility delivers a swift, unified perspective within minutes.
Also The Getvisibility Endpoint Data Classification Solution is designed to help your organization classify and protect your data in motion with state-of-the-art machine learning algorithms by combining natural language processing with neural networks. The Artificial Intelligence (AI) enabled tool suggests classification to end users of tagging documents and emails but also learns from users selections, improving accuracy overtime.
Key Solutions Features:
- Classifies Data-in-Motion
- AI/ML based suggestions
- Comprehensive reporting
- Multi-language support
RST Cloud
RST Cloud is an Australian cybersecurity provider offering cutting-edge services in the field of cyber threat intelligence (CTI). RST Cloud leverages top-notch technologies to enhance the quality of CTI knowledge, making it actionable and maximally usable for companies worldwide.
The RST Cloud engine seamlessly integrates AI and ML technologies to streamline the translation of human-readable cyber threat reports into STIX 2.1 format. This process, once considered a technical challenge, has been effectively addressed through the deployment of advanced AI algorithms, machine learning models, and automation expertise by the RST Cloud technical team.
Despite the inherent complexities associated with implementing and supporting such technology, such as unstructured and diverse source data formats, challenging data and relationship classification, and identification, RST Cloud has successfully addressed these challenges. Through a combination of automation, machine learning, and artificial intelligence, this powers the transformation, paving the way for enhanced efficiency and productivity in SecOps operations.
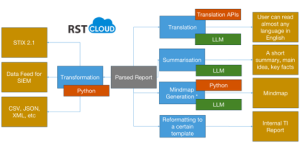
By leveraging these modern technologies and supporting native integration with Palo Alto Cortex XDR, Elastic, Check Point Software Technologies, Fortinet, SAF Systems, OpenCTI, and other security solutions, RST Cloud alleviates the burden of manual report translation tasks. This frees up valuable time for CTI experts to focus on critical analysis and response efforts.
This integration represents a significant step forward in the evolution of threat intelligence, driving innovation and empowering organisations to stay ahead of emerging cyber threats.
Conclusion
The future of cybersecurity hinges on AI, no one can ignore that especially when addressing the large and potential threats posed by social engineering and IoT malware, also we need always to remember that hackers and bad actors leveraging the AI technologies in their attacks so that you need use the same for the defense.
Moreover, before implementing AI into your business, ensure that your employees are well-trained to handle the process to have the best possible protection.




